Begin Solution Implementation (SI) for AMS decision point: #5
(Re-baseline:OMB Exhibit 300, Attachment 1, 2 & 3 for the In-Service Decision (ISD))
Note: The symbol "*" indicates that the FAA firewall access is required to view this link.
Review
- FAAFASTAMS Lifecycle Phases and Decisions guidance website:
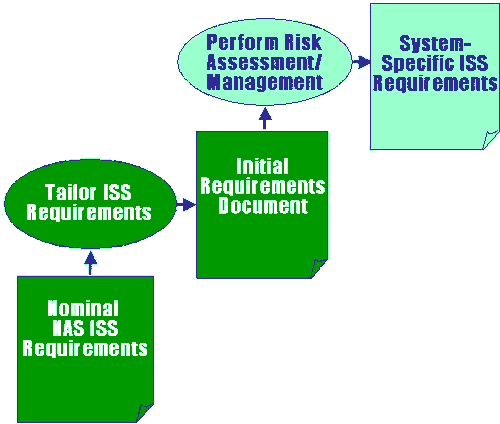
- FAAFASTISS Flow Chart of the SI section
- OMB Exhibit 300, Attachment 1, 2, & 3.
Update
- Security information for Solicitation Information Request (SIR), Contract Statement of Work (SOW) and Contract Data Requirement List (CDRL).
- Vulnerability and risk assessment for the Security Risk Assessment (SRA).
- This is to be performed independent of the Integrated Product Team (IPT).
- “Update Vulnerability and Risk Assessment” (f)
- CONOPS of system.
- “Update the CONOPS and Security Requirements” (g)
- To include ISS section to the CONOPS depending on level of impact of the NAS system.
- ISS section for the Final Requirement Document (fPR).
- Security Interfaces document for inclusion in Interface Requirement Document (IRD).
- “Integrate Security Requirements with System Requirements” (h)
- “Integrate Security Architecture and Design” (i)
- The ISSP.
- “Update the ISSP” (j)
- SCAP to reflect actual fielded systems with your Service Unit/Service Area Certification Team Lead and ISSO. Must complete the SCAP documents before operating the system.
- Locate the “ATOISS Implementation Guide * ” and follow the link “SCAP” for the SCAP guidance document.
- “Create Final Security C&A Documents” (n)
Generate
- Security testing on system baseline and refine solution as needed for ISD/commissioning.
- This is to be performed independent of the IPT.
- “Develop Security Test Plans and Procedures” (k)
- Users guide, training plans, and contingency/disaster recovery plans.
Obtain
- DAA signature(s) of Certification and Authorization to connect and operate system in the NAS.
- “Obtain Security Authorization and Accreditation” (o)
- ATO Designated Approving Authority (DAA), Information System Security Certifier (ISSC), and Information System Security Manager (ISSM).
- “Obtain Security Authorization and Accreditation” (o)
Deliverables
- SCAP Implementation Guide(Reference: SCAP implementation guide - Section 4.1.1 *)
- Baselined OMB Exhibit 300, Attachment 1:
- ISS section of the Final Requirement Document(fPR).
- Security Interfaces in the IRD.
- ISS section of the Final Requirement Document(fPR).
- Baselined OMB Exhibit 300, Attachment 2, & 3
- The security information for SIR, SOW & CDRL.
- DAA signature(s) of Certification and Authorization to connect and operate the system in the NAS.
End SI for AMS decision point: #5 & AMS Phase: SI