Integrate Initial Security Needs and Threat Stipulation into the MNS (a)
Wednesday, November 27, 2024AMS Lifecycle Phase:Mission Analysis >>> Service Analysis
Description
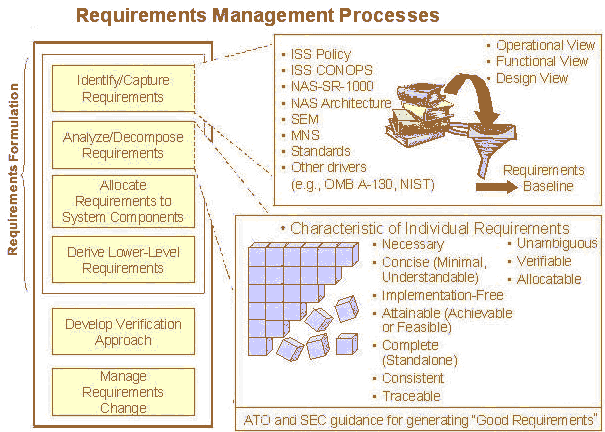
The needs determination is the evaluation of the capacity of an organization's assets to satisfy existing and emerging demands. The traditional components of needs determination are establishing a basic system idea, preliminary requirements definition, feasibility assessment, technology assessment, and a formal approval to investigate further. The same holds true for security needs.
The list below provides an example of the perceived threats to the NAS:
- Intrusion or unauthorized access to system resources
- Insertion of malicious code, software/hardware, or database modification
- Exploitation of known software weaknesses
- Corruption by system, system errors, or failures
- User abuse or fraud
- Inadvertent acts of carelessness
- Natural disasters
- Saturation of communications or resources
- Theft, sabotage, vandalism, or physical intrusion
- Physical cable cuts
- Jamming (telecomm)
- Installation errors
- Eavesdropping or shoulder surfing
- Data entry errors or omissions
- Misrepresentation of identity/impersonation
- Environmental conditions
- Improper disposal of sensitive media
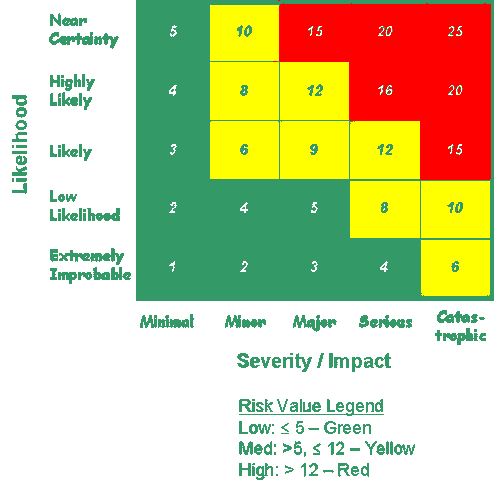
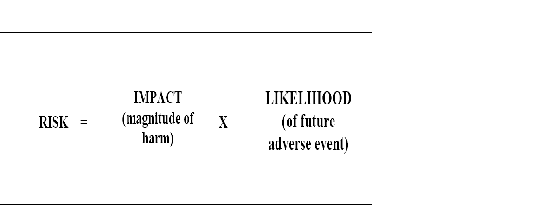
Note: During this early phase of the system's development, the security needs determination will give better understanding of the Information Systems Security assurance requirements. The security implications of alternatives should also be considered during the Concept & Requirements Definition (CRD) lifecycle phase. In this stage you must locate your Certification Lead (CL) and Information System Security Officer (ISSO) within your program office. They may assist and guide you through your determination level of efforts on the security activities that result in the overall development of the SCAP document. If there is an SCAP for the existing system then do either an annual update or the re-SCAP. Review the document, ATO - Information Systems Security Program Implementation Guide (SCAPs) and consult with your program office for this activity.
Tasks
- Locate your Program Office CL and ISSO
- Review and become familiar with the Resources listed below
- Review the document ATO - Information Systems Security Program Implementation Guide (SCAPs) for overall information
- Determine the security needs of the program
- Trade studies to find most appropriate possible solutions
Resources
- Homeland Security Presidential Decision Directive - 7, Critical Infrastructure Identification, Prioritization, and Protection
- OMB Circular A-130, Management of Federal Information Systems, Appendix III
- 44 USC 35, Subchapter II, Federal Information Security Management Act (FISMA)
- Federal Information Security Management Act (FISMA), PL 107-347, Title III
- FAA Order 1370.82A, Information Systems Security Program
- NIST Special Publication 800-12, An Introduction to Computer Security - The NIST Handbook
- NIST Special Publication 800-14, Generally Accepted Principles and Practices for Securing Information Technology Systems
- NIST Special Publication 800-18, Guide for Developing Security Plans for Information Technology Systems
- NIST Special Publication 800-23, Guidelines to Federal Organizations on Security Assurance and Acquisition - Use of Tested/Evaluated Products
- NIST Special Publication 800-27, Engineering Principles for Information Technology Security (A Baseline For Achieving Security)
- NIST Special Publication 800-30, Risk Management Guide for Information Technology Systems
- NIST Special Publication 800-35, Guide to Information Technology Security Services
- NIST Special Publication 800-36, Guide to Selecting Information Technology Security Products
- NIST Special Publication 800-47, Security Guide for Interconnecting Information Technology Systems
- NIST Special Publication 800-51, Use of the Common Vulnerabilities and Exposures Vulnerability Naming Scheme
- NIST Special Publication 800-53, Recommended Security Controls for Federal Information Systems
- NIST Special Publication 800-55, Security Metrics for Information Technology Systems
- NIST Special Publication 800-60, Guide for Mapping Types of Information and Information Systems to Security Categories
- NIST Special Publication 800-61, Computer Security Incident Handling Guide
- NIST Special Publication 800-64, Security Considerations in the Information System Development Life Cycle
- FIPS Publication 140-2, Security Requirements for Cryptographic Modules
- FIPS Publication 199 - Standards for Security Categorization of Federal Information and Information Systems
- FAA Systems Engineering Manual (SEM)
- FAA Acquisition System Toolset (FAST)
- NAS SR-1000, security section
- ATO - Information Systems Security Program Implementation Guide (SCAPs)
- ATO - Information Systems security Architecture (ISSA). Latest version
- FAAISS Handbook