AMS Lifecycle Phase: Investment Analysis >>> Initial Investment Analysis
Description
Vulnerabilities are weaknesses in the physical layout, organization, procedures, personnel, management, administration, hardware, or software that may be exploited to cause harm to system. The goal of the preliminary vulnerability assessment is to develop a list of system vulnerabilities (flaws or weaknesses) that could be exploited by a potential threat. For new systems, the search for vulnerabilities should focus on security policies, planned procedures, system requirements definitions, and security product analysis. For operational systems, analyze technical and procedural security features and controls used to protect the system. Vulnerability analysis encompasses the following five security control areas:
- Technical - hardware, software, system architecture, and modes of communication
- Operational - procedures that people perform with respect to an information system
- Administrative - weak countermeasures in the administrative procedures that affect information systems
- Physical - weak countermeasures in the physical layout of, and access to, facilities and enclosures where automated information systems are housed
- Personnel - weak countermeasures in policy, process, and procedures used for security screening of staff having access to the system
After analyzing the technical, operational, administrative, physical, and personnel controls on the system, the vulnerabilities are paired with specific threats to create a set of vulnerability-threat pairs. The next step is to analyze vulnerability-threat pairs and to identify and determine which existing system countermeasures reduce or mitigate specific vulnerabilities. This is the beginning of the risk assessment process.
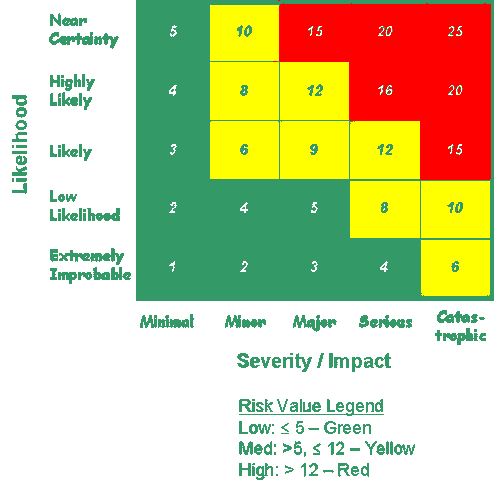
Risk can be thought of as the combination of the severity of vulnerability and the likelihood that the vulnerability will be exploited.
R = L * I
Where R is the Risk, L is the Likelihood of a vulnerability being exploited and I is the Impact (or severity) of exploiting the vulnerability. The result of this combination is a risk rating. Risks can then be mitigated based on the overall risk rating. The table below is used when determining whether a risk is low, medium, or high. All high-level risks should be mitigated before medium or low level risks. Once all high risks have been mitigated, additional risks can be mitigated, based on schedule, funds, and ability of mitigation to mediate the risk(s).
The preliminary risk assessment should result in a brief initial description of the basic security needs of the system. In practice, the need for information security protection is expressed in terms of the need for integrity, availability, and confidentiality and other security needs that may be applicable (accountability, non-repudiation). Integrity can be examined from several perspectives. From a user's or application owner's perspective, integrity is the quality of data that is based on attributes such as accuracy and completeness. From a system's or operation's perspective, integrity is the quality of data that it is only changed in an authorized manner or that the system/software/process does what it is supposed to do and nothing more. Like integrity, availability also has a multipart definition. Availability is the state when data or a system is in the place needed by the user, at the time the user needs it, and in the form needed by the user. Confidentiality is the privacy, secrecy, or nondisclosure of information except to authorized individuals.
A preliminary risk assessment should define the threat environment in which the product or system will operate. This assessment is followed by an initial identification of required security controls that must be met to protect the product/system in the intended operational environment. The risk-based approach to information security is defined in NIST Special Publication 800-30, Risk Management Guide for Information Technology Systems.
The risk assessment should be done before the approval of design specifications. The preliminary risk assessment may not be a large and complex document; however, it should take into account existing controls and their effectiveness. The risk assessment should identify any deficiencies in t eh analysis of integrity, confidentiality, and availability requirements or the security assurance requirements analysis by demonstrating the logical conclusion of the analyses.
The preliminary vulnerability and risk assessments should be combined into one final document that addresses the systems vulnerabilities and risks. At the completion of this step, the Product Team will have a general understanding of the security issues facing the system. As more details are known about the system, an updated vulnerability and risk assessment can be completed to uncover new areas of risk to the system.
Tasks
- Gather information on the system's processing environment
- Review the POAMS and the information from the Department of Transportation (DOT) Enterprise Security Portal (ESP)
- Review industry sources to identify application and hardware specific vulnerabilities
- Identify the threats to and vulnerabilities in the information system
- Identify the potential impact or magnitude of harm that a loss of confidentiality, integrity, or availability would have on assets
- Identify and analyze the security controls for the information system
Resources
- NIST Special Publication 800-30, Risk Management Guide for Information Technology Systems
- NIST National Vulnerability Database
- Department of Transportation (DOT) Enterprise Security Portal (ESP)
- FAA's ISS Handbook
Last updated:
