AMS Lifecycle Phase: Investment Analysis >>> Initial Investment Analysis
Description
After needs have been determined, the list of alternative(s) in CRD was determined and the system should be categorized as to what level of potential impact a security breach would have. Security categorization assists the product teams in making the appropriate selection of security controls for the program.
The system characterization is the central document in the SCAP. Developed by the System Owner, its purpose is to provide a single document that contains relevant system description information, including system architecture, interfaces, data/information types, and the general system operations and maintenance environment in sufficient detail for the reviewer to gain a reasonable understanding of the system and its operating environment. It is important that logical network diagrams be included to provide an opportunity to view the conceptual composition of the system/network. By using logical diagrams in conjunction with the design description, reviewers will be provided with a comprehensive understanding of the system/network design, requirements, goals, and plan for projected growth.
FIPS 199, Standards for Security Categorization of Federal Information and Information Systems, guides the determination of the potential magnitude of harm resulting from a NAS security incident. FIPS 199 categorizes "High," "Moderate," and "Low" impacts of losses of availability, integrity or confidentiality. The assessed categorization provides the impact variable used as a multiplier of likelihood in the ISS Program Handbook risk assessment model:
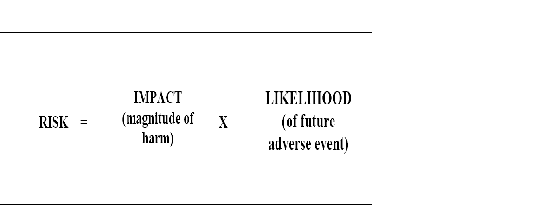
Note: During this phase of the system's development, the security needs determination and categorization should result in a high-level description of the security controls (800-53) in the proposed system to meet the assurance requirements. NIST SP 800-53 is separated into management, operational and technical control that ensures the confidentiality, integrity and availability (CIA) of the system. Check into the latest version of the NIST 800-53 and ISSA for security controls for methodologies on selection and allocation.
Tasks
- Define the security categorization of the program
- Determine the system and its boundaries
- Develop a high level description of the security controls
Resources
- NIST Special Publication 800-64, Security Considerations in the Information System Development Life Cycle
- NIST FIPS199, Standards for Security Categorization of Federal Information and Information Systems
- NIST Special Publication 800-53, Recommended Security Controls for Federal Information Systems
- Federal Information Security Management Act (FISMA), PL 107-347, Title III
- FAA Order 1370.82A, Information Systems Security Program
- OMB Circular A-130, Management of Federal Information Systems, Appendix III
- ATO Information Systems Security Program Implementation Guide (SCAPs)
- ISSA latest version
Last updated: Friday, October 12, 2018
